About User IDs
Optional User IDs can be used to limit conference participation to specific individuals, to better identify participants, or to collect a numeric code from your participants. The most common use is to pre-assign a unique User ID to each invited participant, which the caller will need to enter to join your conference calls. This approach allows you to limit attendance to only those participants with a valid User ID code, such as paid members or authorized personnel.
With User IDs enabled, all participants are prompted to enter a User ID after they have entered the Conference ID. (Note that User IDs may also be used in conjunction with the codeless entry feature associated with the Custom Number Option, which bypasses the requirement to enter the Conference ID code. In this scenario, participants would only need to enter the User ID code.)
User IDs may have any number of numeric digits (including a single digit), and may vary in length. It is generally best to avoid leading zeroes with User IDs.
There are three options for validating User IDs, which can be specified via the “Require User IDs” drop-down selection box in the Settings tab in the Host Control Panel:
- No — Participants will not be prompted to enter a User ID. (This is the system default setting.)
- Valid User ID Required — Participants must enter a valid pre-assigned User ID to join your conferences. The list of valid User IDs is specified via the User IDs tab in the Host Control Panel or by using the setBridgeUserID API with the TurboBridge API. If a caller fails to enter a valid User ID after five attempts, the caller will be automatically terminated. Note that multiple participants may enter the same User ID and join the same conference call.
- Valid User ID Optional — In this scenario, all callers are prompted to enter a User ID. If the caller presses the pound key without entering a code, the caller will be placed into the conference without a User ID. However, if the caller enters a code, it must be a valid User ID in order to join the conference. This option allows you to positively identify particular callers, without preventing others from joining the conference. Since one of the User ID parameters is to automatically designate specific User IDs as Hosts, this approach allows you to extend host privileges without sharing the secret Host PIN with those participants. (Hint: You may wish to establish 0 as a valid User ID, since callers who do not have a User ID may press 0, followed by the pound key.)
- User ID Required, Not Validated — All callers are prompted to enter a User ID, but the code is not validated against the User ID list. However, callers must enter a code (0 is a valid code) to join the conference. This approach allows you to collect numeric input from participants when they arrive (could be a member code or call-back telephone number), but you need to instruct your invited participants in advance. The prompt will ask for a “User ID”, so your invitees will need to know how they should respond.
If User IDs are enabled, the entered User ID value will be displayed in a column in the Live Conference tab in the Host Control Panel. The displayed Name will be the name associated with the User ID listing, not the Caller ID name normally associated with the caller's phone number.
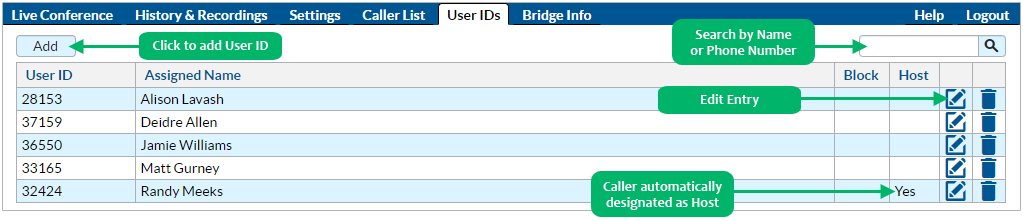
Creating and Editing User IDs. The User IDs tab in the Host Control Panel allows you to create, edit, or delete User IDs associated with your bridge. (The User ID list is associated with a specific Conference ID.) Click on the  button to change the name, automatically designate the caller as a Host, block the caller from participation, or add reference notes.
button to change the name, automatically designate the caller as a Host, block the caller from participation, or add reference notes.
Restricting Duplicate User IDs. Please contact us to request an override setting to prevent more than one participant from joining the conference with the same User ID. We generally advise against this restriction, since there is no assurance that the first party to enter the User ID is the “authorized” participant. A better approach may to use the Live Conference Manager in the Host Control Panel to identify duplicate User IDs, and move each party into a subconference to have a private conversation to verify the caller's identity, and drop an unauthorized participant from the conference.